Cybersecurity Insights

How to Run a Tabletop Exercise for Cybersecurity Preparedness
Learn how cybersecurity tabletop exercises help Australian organisations test incident response plans, improve team readiness, and uncover vulnerabilities without risking live systems.

Privacy by Design Principles: Embedding Privacy into Every Layer
Discover how Privacy by Design principles help Australian businesses embed privacy and data protection into systems and processes from the start, ensuring trust and compliance.

What Is a Privacy Impact Assessment and Why Your Business Needs One
Learn how a Privacy Impact Assessment (PIA) helps Australian organisations identify, assess and mitigate privacy risks, ensuring compliance and best practice for new technologies and data processes.

How to Create an Effective Incident Response Plan
When a cyber incident strikes, every second counts. An incident response plan is a structured, strategic approach to identifying, containing, and resolving cyberattacks or data breaches. Without one, Australian organisations risk significant financial, operational, and reputational damage.

Understanding the Essential Eight Maturity Model: A Non-Technical Guide for Australian Businesses
The Essential Eight Maturity Model is a cybersecurity framework developed by the Australian Signals Directorate (ASD) through the Australian Cyber Security Centre (ACSC). It provides a step-by-step guide for Australian businesses to implement eight critical mitigation strategies that dramatically reduce the risk of cyber incidents.

How to Achieve Data Privacy Compliance in Australia
With increasingly strict privacy laws and public demand for transparency, data privacy compliance is no longer optional — it’s a core responsibility. Australian businesses must understand their legal obligations and implement practical safeguards to protect personal information.

Building a Cybersecurity Governance Framework That Works
As cyber threats grow in scale and complexity, organisations must go beyond technical controls. A cybersecurity governance framework provides the structure to ensure that security aligns with your business strategy, risk appetite, and regulatory obligations.

Compliance Risk Management in Cybersecurity
Cybersecurity today is no longer just a technical function — it’s a compliance priority. Australian organisations are facing rising regulatory scrutiny, and compliance risk management has become a critical element of cybersecurity strategy.

Top Business Cyber Threats Being Faced in Australia Today
From targeted phishing to sophisticated ransomware campaigns, business cyber threats in Australia are more prevalent, more disruptive, and more financially damaging than ever. Understanding today’s most serious threats is the first step toward reducing your organisation’s exposure.
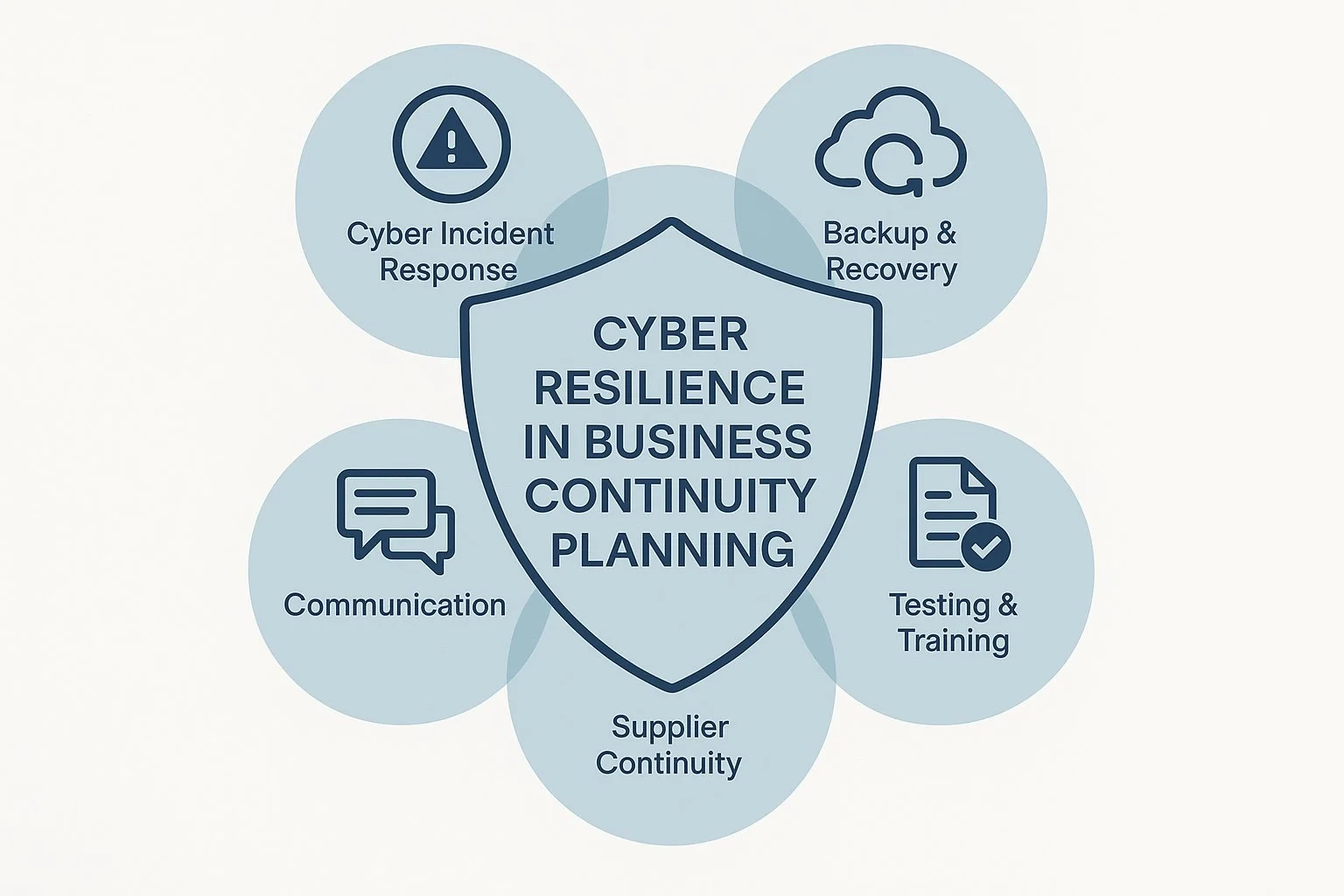
How to Build Cyber Resilience into Your Business Continuity Plan
Learn how to build cyber resilience into your business continuity plan to protect critical operations from ransomware, data breaches, and disruptive attacks — keeping your organisation compliant, prepared, and ready to recover fast.
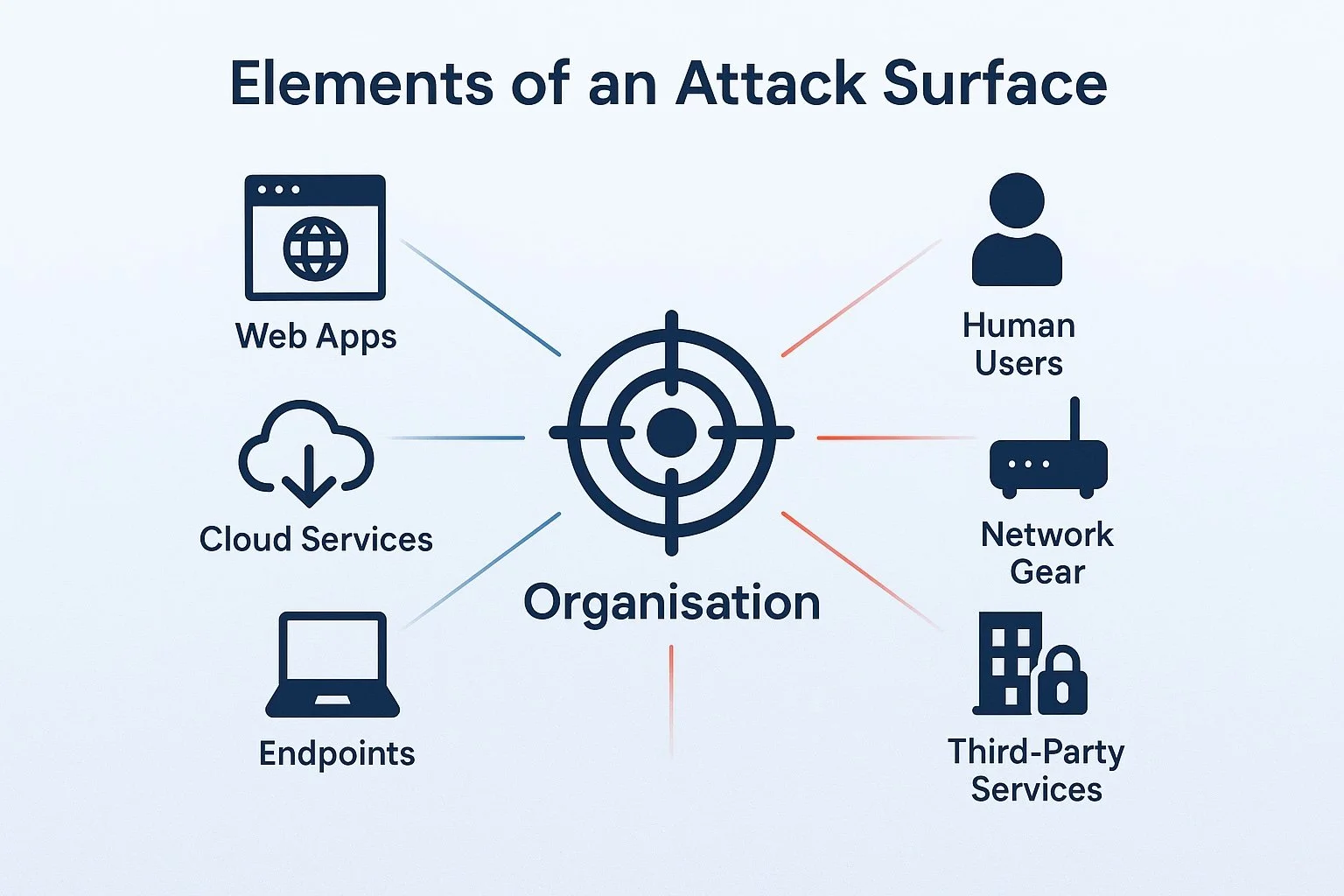
What is Attack Surface Management and Why It Matters
Attack surface management identifies, measures, and reduces weak points to strengthen your cyber defences and protect your environment - Understand your organisation’s vulnerabilities before attackers do.
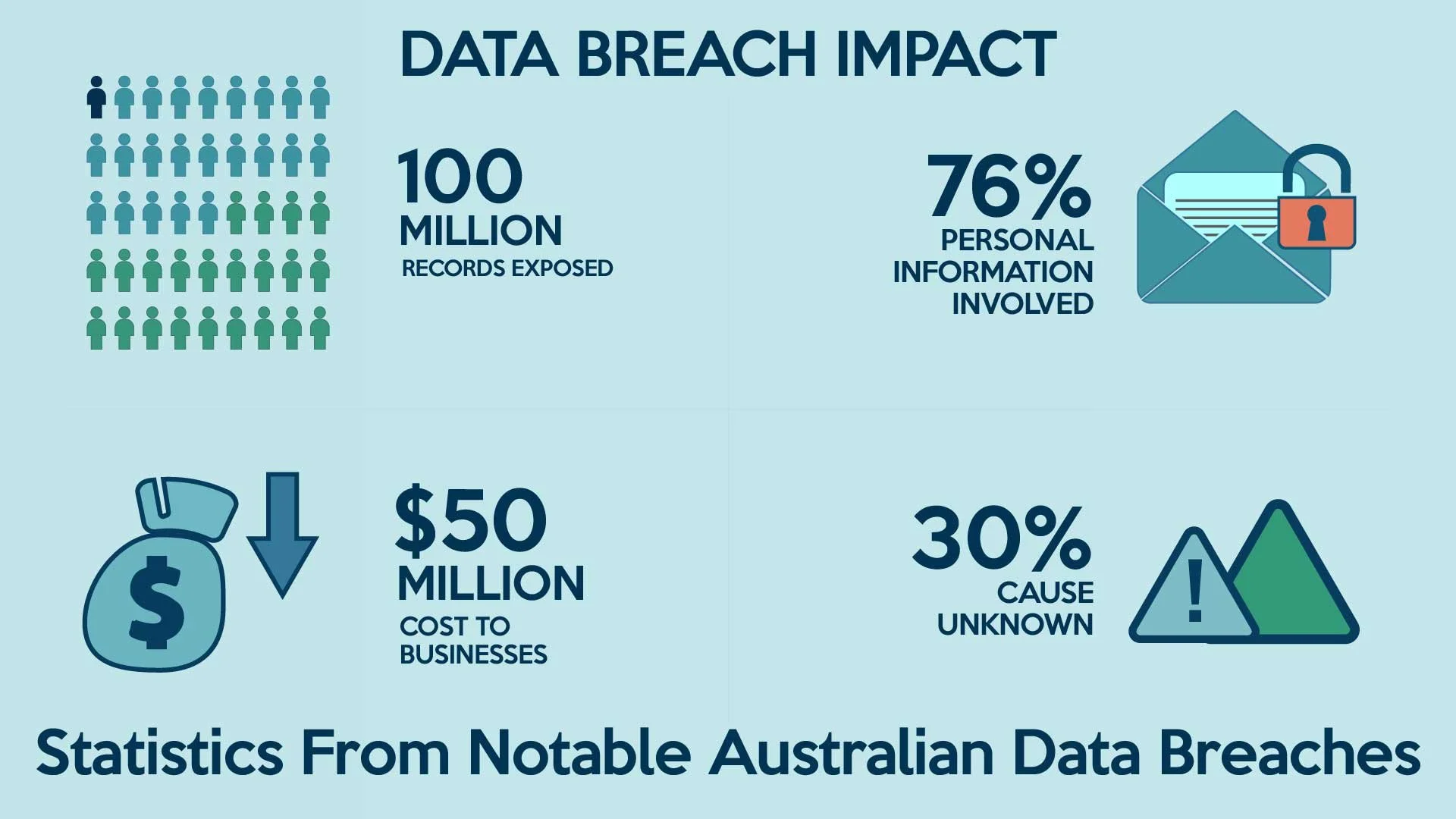
Understanding the Notifiable Data Breaches Scheme in Australia
Australia’s Notifiable Data Breaches Scheme mandates businesses to report eligible data breaches. This article explains your obligations, how to respond effectively, and how to minimise legal and reputational risks.

Understanding APRA CPS 234 Compliance for Australian Businesses
For Australian financial institutions and other APRA-regulated entities, APRA CPS 234 compliance is a critical part of cybersecurity governance. This standard sets out how organisations must manage information security to protect themselves — and the broader financial system — from cyber threats.
