What is Attack Surface Management and Why It Matters
Attack Surface Management Matters
All systems have their weak points.
Attack Surface Management
Every system has weak points — the question is whether you know about them before an attacker does. Attack surface analysis helps you map, measure, and reduce the pathways a threat actor could use to breach your environment. It’s a critical part of proactive cybersecurity.
What is Attack Surface Management?
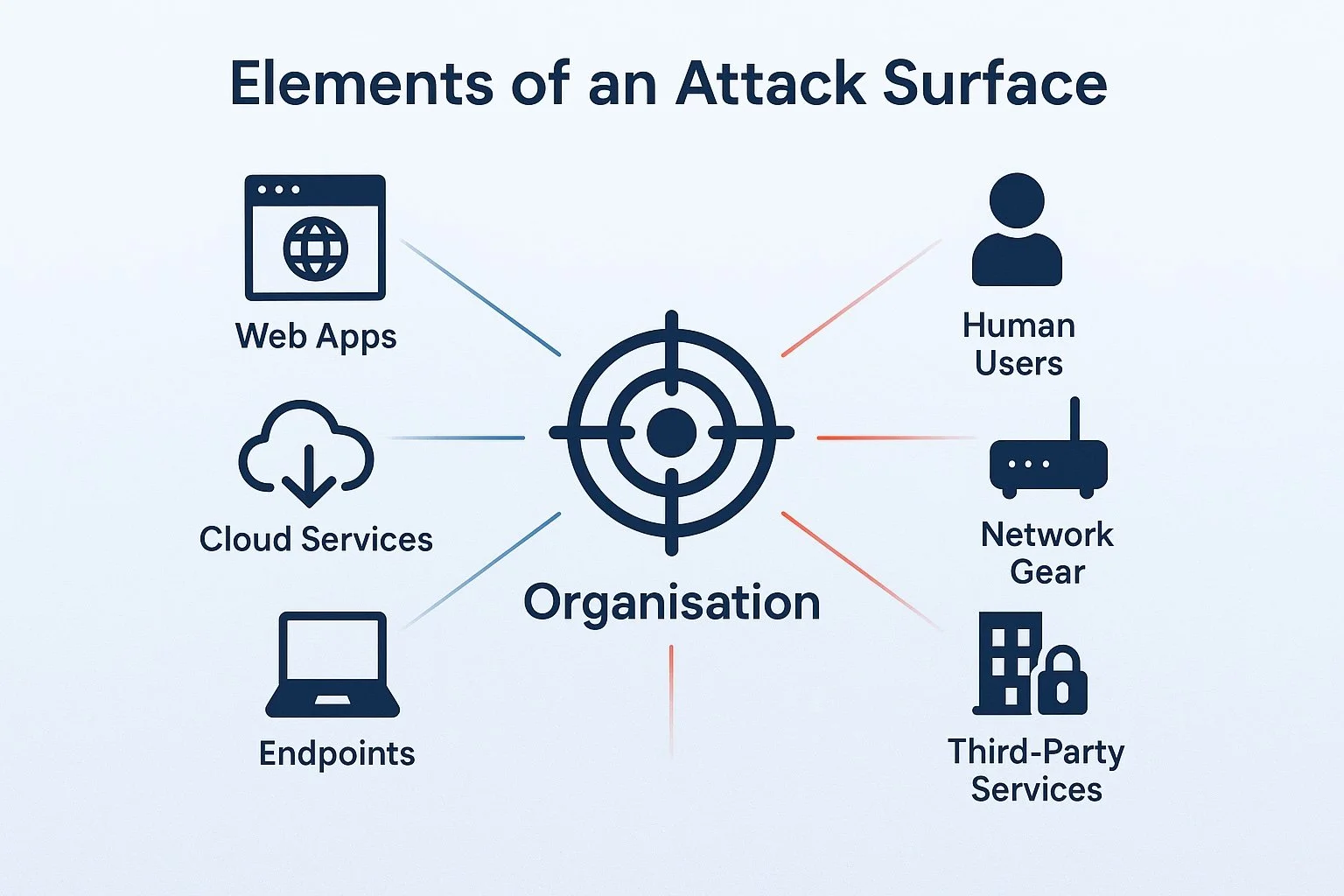
Attack Surface Management (ASM) is the process of identifying and evaluating all the potential entry points into an organisation’s IT environment. These can include:
- Public-facing websites and services
- APIs and mobile applications
- Remote access portals
- Email and cloud platforms
- Outdated software, exposed ports, or misconfigurations
- Human elements like phishing and social engineering targets
Your attack surface is not static — it grows and changes with every new device, user, service, or integration.
Why It’s Important
Attack surface analysis allows organisations to:
- Detect unknown assets and exposures
- Prioritise high-risk vulnerabilities
- Inform patching, segmentation, and access control strategies
- Support threat modelling and red team exercises
- Prepare for compliance audits and incident response
The Australian Cyber Security Centre (ACSC) recommends continuous asset discovery and external scanning as foundational practices in its Essential Eight and cyber hygiene guidance.
Components of an Attack Surface
1. Digital Assets
Web servers, CMSs, databases, mobile apps, and SaaS platforms
2. Network Infrastructure
Routers, switches, firewalls, VPN gateways, and load balancers
3. Endpoints
Laptops, desktops, IoT devices, unmanaged personal devices (BYOD)
4. Human Attack Surface
Employees, contractors, and vendors susceptible to phishing or impersonation
5. Third-Party Exposure
Integrations with suppliers, vendors, and cloud service providers
Tools for Attack Surface Analysis
External Attack Surface Management (EASM) platforms: e.g. Palo Alto Cortex Xpanse, Microsoft Defender EASM
Open-source tools: Nmap, Shodan, Amass, OWASP ZAP
Vulnerability scanners: Qualys, Nessus, Rapid7
Asset discovery tools: Lansweeper, Fing, and Active Directory integrations
Steps in the Analysis Process
Inventory All Assets
Start with domain names, IP ranges, DNS records, and cloud resources.
Scan and Identify Vulnerabilities
Use automated scanners to find outdated software, misconfigurations, and exposed services.
Classify and Prioritise
Not all exposures are equal. Prioritise based on exploitability and asset criticality.
Remediate and Harden
Apply patches, close unused ports, disable insecure protocols, enforce MFA.
Monitor Continuously
Attack surfaces are dynamic. Implement ongoing monitoring and alerting.
Final Thoughts
If you don’t know your attack surface, you can’t defend it. Attack surface management gives organisations visibility, prioritisation, and control — all essential in today’s fast-moving threat landscape.
Make ASM a routine, not a reaction.