How to Build Cyber Resilience into Your Business Continuity Plan
BUSINESS CONTINUITY PLANNING
Cyber Security Needs to Be Part of it
Business Continuity Cyber Attack
In the event of a cyber attack, your ability to maintain or quickly restore operations can mean the difference between survival and shutdown. Integrating cybersecurity into your business continuity plan ensures your organisation is not only prepared for natural disasters or power failures — but also for ransomware, data breaches, and denial-of-service attacks.
Why Cybersecurity Must Be Part of Business Continuity
Traditional business continuity plans often focus on physical threats. However, cyber incidents are:
- More frequent
- Harder to predict
- Potentially more damaging (due to data loss, regulatory fines, and reputational harm)
The Australian Cyber Security Centre (ACSC) and APRA CPS 234 both stress that cyber risks must be incorporated into business continuity and disaster recovery planning.
Key Cyber Risks That Threaten Business Continuity
- Ransomware locking critical systems or databases
- Data breaches triggering legal and compliance action
- DDoS attacks making services unavailable
- Malicious insiders causing operational sabotage
- Third-party supplier compromise impacting dependencies
These threats demand coordinated, pre-tested response capabilities across technical, legal, and executive functions.
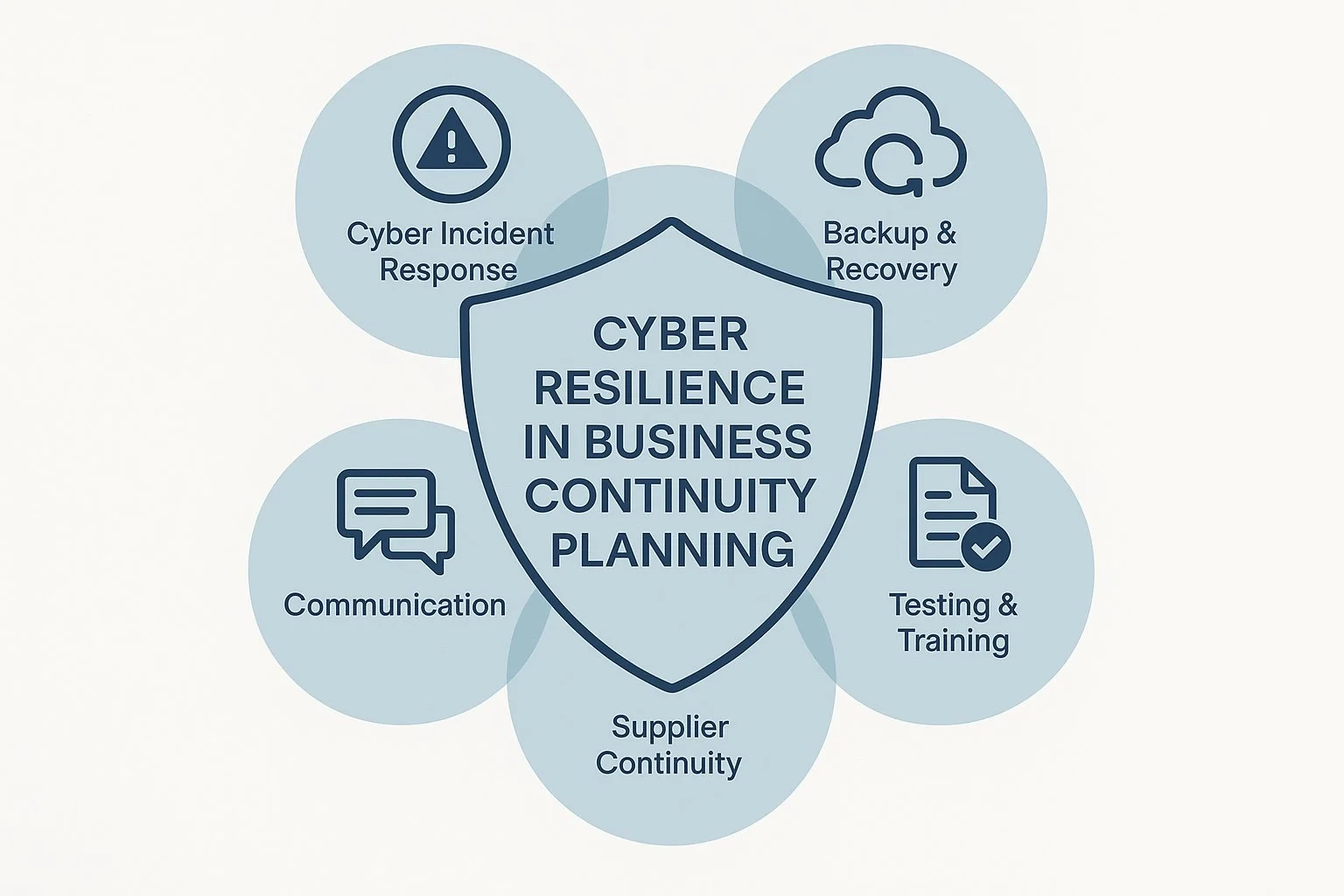
Steps to Integrate Cyber Resilience into BCP
1. Risk Assessment
Identify high-risk digital assets and services. Understand which systems, data, and processes are mission-critical.
2. Cyber Incident Response Planning
Have a documented and tested response plan for cyber incidents. Align it with your business continuity strategy.
3. Backup and Recovery Strategy
Use the 3-2-1 backup rule: 3 copies, 2 different media, 1 offsite/offline.
Test your backup recovery frequently.
Ensure encryption and access controls on backup systems.
4. Communication Plan
Include cyber scenarios in your internal and external communication strategies. Define how you’ll notify:
- Employees
- Customers
- Regulators (e.g. OAIC under the Notifiable Data Breaches Scheme)
5. Tabletop Exercises
Conduct regular cyber incident simulations to test decision-making, technical response, and business recovery capabilities.
6. Third-Party Risk Management
Evaluate and test the continuity of external vendors, especially those with access to your systems or data.
Compliance and Industry Guidance
Cyber-integrated BCP supports compliance with:
- APRA CPS 234 and CPS 232 (Business Continuity Management)
- ISO 27031: ICT readiness for business continuity
- Essential Eight Maturity Model recommendations for recovery strategies
Final Thoughts
Business continuity planning is no longer complete without cybersecurity integration. As cyber attacks become more sophisticated and disruptive, resilient organisations will be those that anticipate, simulate, and recover — fast.
A cyber attack is not just an IT issue. It’s a business survival issue.